



My final year project, developed over two semesters of my fourth year, encompasses a suite of documentation and a fully functional system: the Unified Vulnerability and Management System. As this project was so large, you can click here to read more information on it.
The web application automates and also manages vulnerability scans by integrating tools like Nmap, OPEN-VAS, and ZAP. It simplifies complex scans so they are more user-friendly, outputs the results to a database, and compiles comprehensive reports in PDF format.
The system features four specialised dashboards, each designed for distinct user roles: System Administrators, Penetration Testers, Analysts, and Engineers. This role-based architecture ensures that each user has the necessary tools to efficiently perform their duties, from managing user accounts and configuring scans to triaging results and focusing on vulnerability remediation. The project is fully open source.
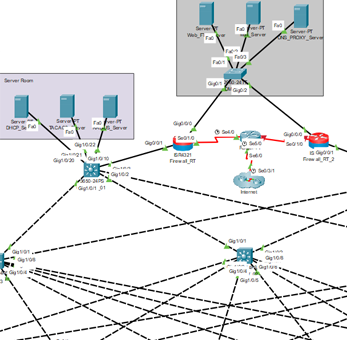
During the first semester of my networking module, I was given a project that required the use of Cisco Packet Tracer that would provide 30% of my overall networking grade. The project entailed designing and implementing a sophisticated simulated network infrastructure at the SETU Kilkenny campus, aimed at enhancing security, performance, and manageability. This included developing a VLAN-based architecture to efficiently separate network traffic for 255 simulated users across different user types, improving network performance and security. To accommodate the varying user requirements, I configured dynamic IP address allocation via DHCP, incorporating security measures such as, hardening, snooping and firewalls to mitigate potential vulnerabilities.
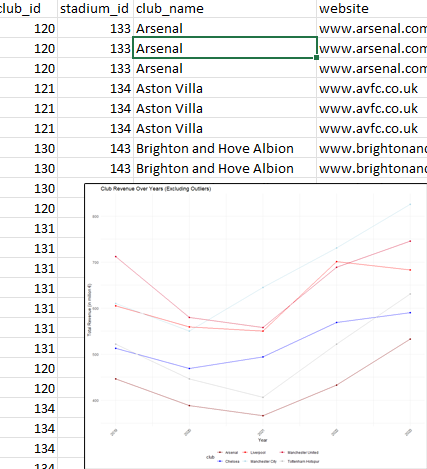
This project was split into two parts, with the first part being a report focused on the importance of data visualisation, specifically how it can enhance malware analysis. Through desk-based research across different sources, my paper provides an evaluation of how data visualisation can improve both malware detection and analysis.
The second part of the project was more hands-on: Money and Management: Evaluating Their Roles in Premier League Success. This project, chosen from personal interest, involved analysing the impact of financial investment and managerial effectiveness on team performance in the Premier League. I used Excel and Tableau to create visuals and construct a narrative around a research question, applying data manipulation to draw conclusions. The report and markdown can be found below
This project involved three key deliverables which centered around Solidity code and a smart contract deployment on the Sepolia blockchain. The first deliverable required implementing the VaultManager smart contract, which included providing implementations for various functions as outlined in a given class diagram. The second deliverable focused on writing a set of test functions in Solidity to ensure comprehensive test coverage for all functionalities within the VaultManager contract. The third and final deliverable was the deployment of the VaultManager smart contract to the Sepolia blockchain, necessitating a deployment script which would provide a contract address for an instance available on Sepolia.
Unfortunately, I cannot share the code for this due to academic integrity, in case the project is repeated in future years.
The deployed contract can be found: here
In my third year, I was given a project that contributed to grades across three modules: Cryptography, Legislation, and Software Engineering. The project was centred around developing an web based application for Ireland's national health service, which allowed people to report positive COVID-19 antigen tests and list their close contacts online.
This required implementing cryptographic techniques to encrypt personal data, such as names and phone numbers, and employing secure methods for password management through hashing and salting. The project demanded an in-depth understanding of GDPR regulations and I had to ensure that the application was fully compliant. The project emphasised "Data Protection by Design" principles, and required the creation of UML diagrams to illustrate how data security and privacy were integral from the initial design stages, and so avoiding potential legal issues in case of a data breache/s.
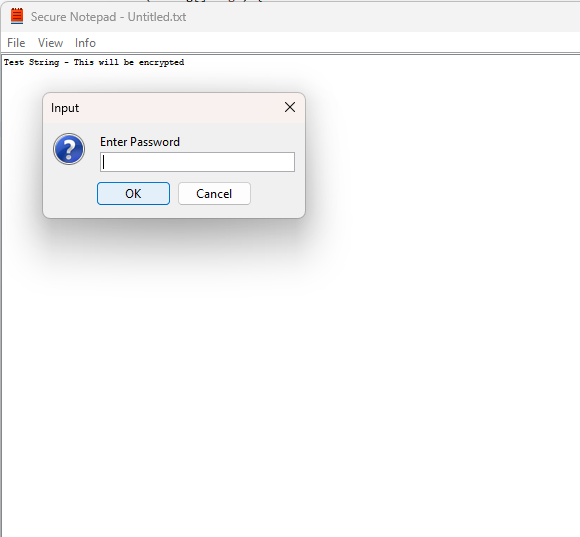
During third year, as part of the Cryptography module, we were assigned a project that involved working with pre-written code provided by our lecturer. This covered the basic functionality and GUI of a typical text editor, similar to Windows Notepad. While this project facilitated understanding of the crypographic implemented, I felt it important to try and attempt this project from scratch myself. I redesigned the SecureNotepad independently, in order to help apply my learnings in a more "hands-on" manner.
The SecureNotepad is a Java-based application which extends JFrame and provides encrypted text editing capabilitiy. It's designed to offer a more secure alternative to traditional text editing by allowing users to encrypt notepad files before saving and requiring decryption upon opening.
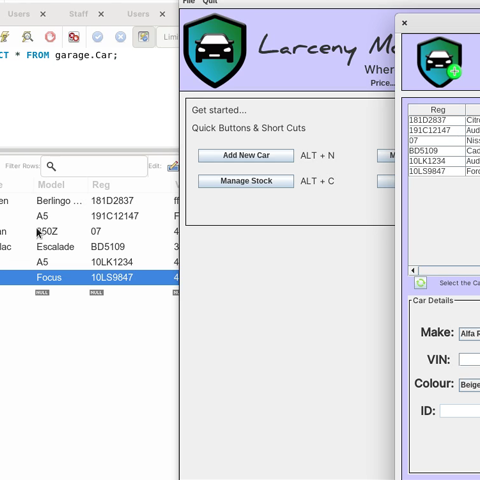
In my second year, we were tasked with a project that involved creating a Java-based front end with a GUI connected to a backend SQL database. I chose to create a car dealership system application, designed to perform full CRUD (Create, Read, Update, Delete) operations. I used Docker to set up the SQL database, enabling a link to my Java GUI for simplicity. The main window served as a hub, where users could access additional windows based on specific actions, each retrieving and displaying relevant data from the database. I also developed a form-based window for users to input data directly into the database, simulating real-world dealership operations.
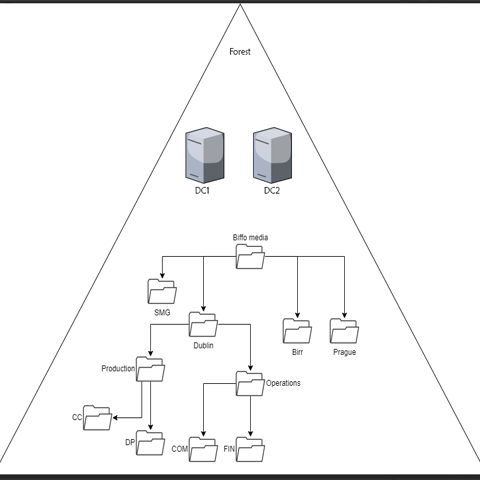
For a project in secure systems administration were tasked with setting up a server layout for a business. The project required us to establish an IP address scheme and perform initial connectivity tests through ping verification for various client systems. We used Virtual box to simulate this. We had to design the Active Directory, starting with an initial AD structure layout and configuring domain controllers. We implemented an Organizational Unit (OU) structure, considering specific organizational needs, and created a OU structure map. Group Policy Objects (GPOs) were required to manage system and security settings across the network. To support network services, we had to configure DHCP with appropriate scopes and performed simulated DHCP client ping checks to verify connectivity. We also implemented DNS to facilitate name resolution across the network. The project further involved setting up a website using Internet Information Services (IIS) which had to be minimum three pages and configured a RAID-5 to ensure data redundancy.